How does a business maintain seamless technology operations while juggling employee needs and customer demands? Who ensures that minor technical glitches don’t snowball into major disruptions? The answer lies...
Why do organisations still rely on the waterfall methodology when agile, DevOps, and iterative models are dominating today’s development space? Is a structured, sequential approach still relevant in fast-paced...
What ensures the reliability of software when teams push code every hour or day? How do organisations manage code conflicts, bug detection, and delivery speed in modern software development...
In today’s interconnected world, cyberattacks are not just a threat, they are a certainty. As businesses increasingly depend on digital platforms to store sensitive data, run operations, and manage...
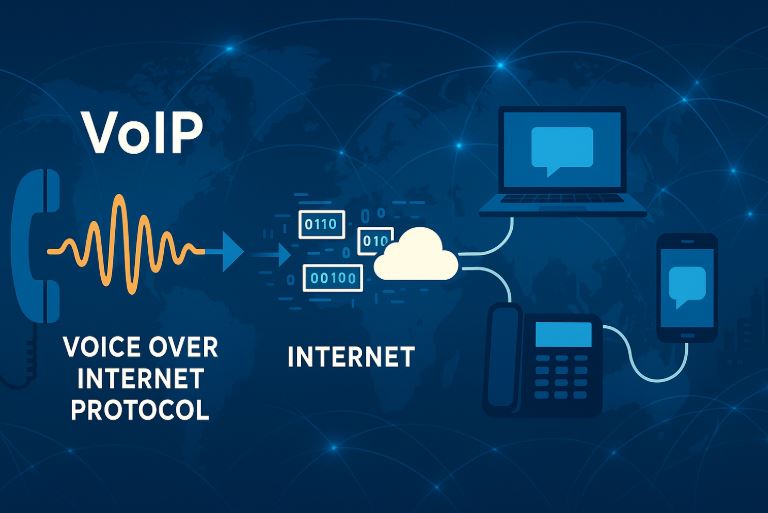
Voice over Internet Protocol, widely known as VoIP, is a foundational technology in modern communications. It allows voice signals to be transmitted over the internet instead of the traditional...
Have you ever received a suspicious email or SMS urging you to update your bank details or click a link urgently? If so, you may have been targeted by...
How do cybercriminals breach even the most secure systems without writing a single line of malicious code? The answer often lies in a social engineering method that manipulates human...