How can secret information move through digital networks without drawing attention? How do hackers conceal malicious payloads inside files that seem entirely harmless? And how do cyber security professionals...
Have you ever considered how easily an attacker could gain access to your most private information without even breaching your firewall? In the vast landscape of cyber threats, keyloggers...
In the ever-evolving world of digital technology, the need to control, monitor, and secure access to information systems is more critical than ever. Cyber threats are no longer isolated...
Why does a decades-old attack method like SQL injection still remain one of the most widely used techniques by cybercriminals in 2025? Why are businesses across the UK and...
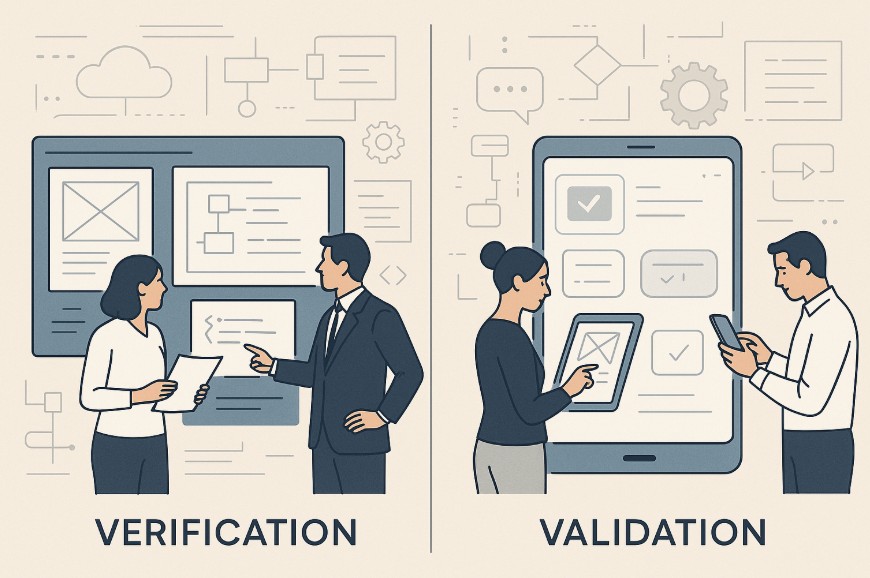
Can software be considered reliable if it hasn’t been meticulously checked for accuracy and functionality? Can developers and stakeholders confidently claim a product is ready for release if no...
How do organisations maintain business continuity while upgrading technology? What steps are necessary to move vast amounts of information from ageing systems to modern cloud infrastructure? These questions are...
What makes a truly competent software developer in today’s technology-driven world? With industries increasingly reliant on digital solutions, software development has evolved beyond writing lines of code. It’s a...
Why do organisations still rely on the waterfall methodology when agile, DevOps, and iterative models are dominating today’s development space? Is a structured, sequential approach still relevant in fast-paced...
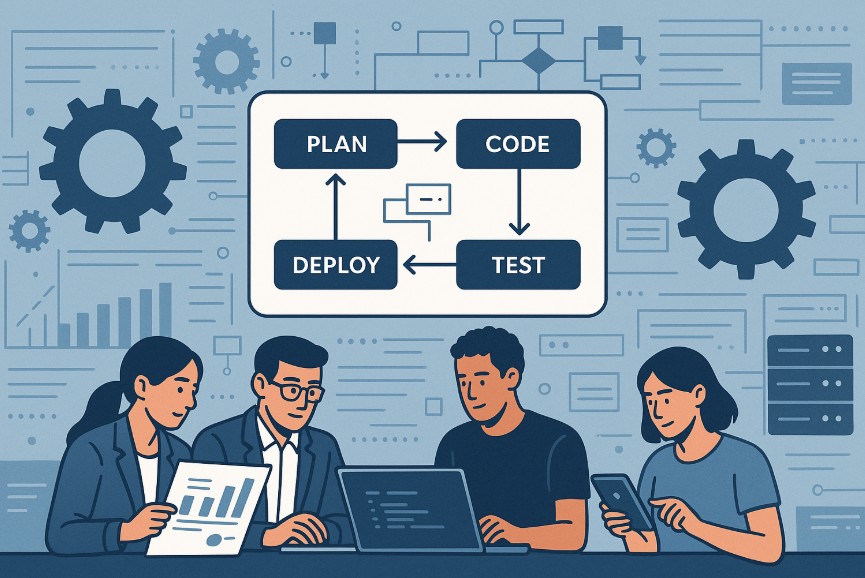
How do software teams consistently deliver applications that are reliable, secure, and aligned with business goals? The answer lies in the use of a structured methodology called the Software...
In today’s increasingly connected world, the ability to access a computer remotely is no longer a luxury but a necessity. Whether you are working from home, supporting clients as...