Have you ever wondered how cyber attackers manage to breach sophisticated security systems despite the most advanced defences? The answer lies in understanding how attacks unfold, step by step....
How can organisations protect their confidential information in an age where cyber threats are advancing faster than ever? What measures ensure that sensitive customer details, financial records, and intellectual...
How do organisations detect hidden cyber threats that slip past traditional defences? How can they stop such attacks before they cause irreversible damage? In today’s evolving digital landscape, malicious...
Have you ever thought about how hackers manage to break into secured systems without exploiting complex software bugs? Surprisingly, they often don’t need to. One of the simplest and...
In an age where data breaches, identity theft, and digital fraud are common, how do organisations create an environment of trust in digital communications? As more services, interactions, and...
How do modern cloud platforms handle unpredictable demand shifts with such precision? What enables a streaming service to accommodate millions of users overnight or an online store to function...
How do modern businesses manage to run hundreds of applications, services, and systems without constantly expanding their physical infrastructure? How is it possible to operate global digital platforms without...
Why Has Responsive Web Design Become a Necessity in Digital Marketing? Have you ever accessed a website from your mobile phone only to find distorted images, overlapping text, and...
What ensures the reliability of software when teams push code every hour or day? How do organisations manage code conflicts, bug detection, and delivery speed in modern software development...
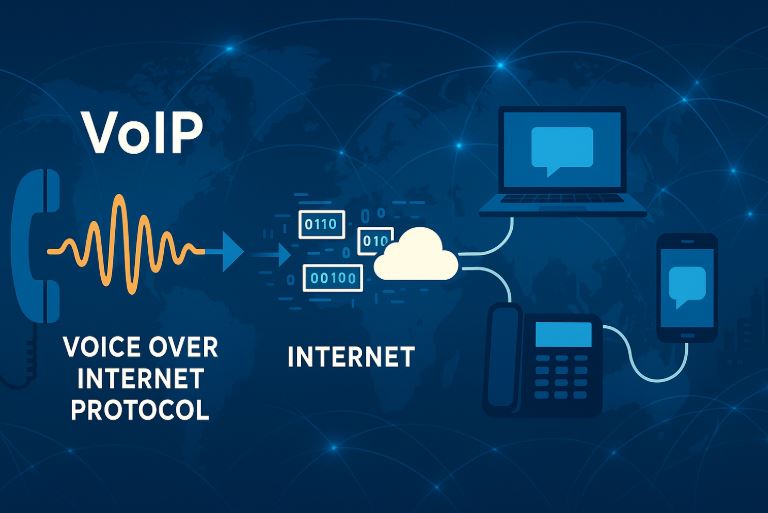
Voice over Internet Protocol, widely known as VoIP, is a foundational technology in modern communications. It allows voice signals to be transmitted over the internet instead of the traditional...