Blog

Have you ever wondered how cyber attackers manage to breach sophisticated security

How can secret information move through digital networks without drawing attention? How

How can organisations protect their confidential information in an age where cyber

Have you ever considered how easily an attacker could gain access to

How Can Ransomware Be Defined in Cyber Security? What happens when the

What Makes a System Vulnerable in the Digital Age? In a world

How do organisations detect hidden cyber threats that slip past traditional defences?

In the ever-evolving world of digital technology, the need to control, monitor,

What Is SIEM? In a digital world where cyber threats evolve faster

Have you ever thought about how hackers manage to break into secured

Why does a decades-old attack method like SQL injection still remain one

Can software be considered reliable if it hasn’t been meticulously checked for

How can software teams keep up with rapid technological changes, unpredictable client

In an age where data breaches, identity theft, and digital fraud are

How can developers build software solutions when user expectations are still unclear?

How do organisations maintain business continuity while upgrading technology? What steps are

How do modern cloud platforms handle unpredictable demand shifts with such precision?

Have you ever tried centering a div or a paragraph in CSS

Have you ever asked yourself how modern companies manage massive amounts of

How do modern businesses manage to run hundreds of applications, services, and

How does a business maintain seamless technology operations while juggling employee needs

What if a single line of poorly validated input on your website

Why Has Responsive Web Design Become a Necessity in Digital Marketing? Have

What happens when a system crash wipes out your data? Would your

What makes a truly competent software developer in today’s technology-driven world? With

Why do organisations still rely on the waterfall methodology when agile, DevOps,

What ensures the reliability of software when teams push code every hour

In today’s interconnected world, cyberattacks are not just a threat, they are

Voice over Internet Protocol, widely known as VoIP, is a foundational technology
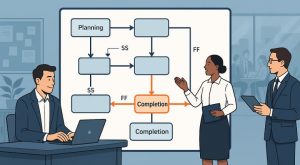
How do project managers ensure every task is completed in the right

In today’s increasingly digital world, businesses, educational institutions, healthcare systems, and governments

In today’s surveillance-heavy digital age, concerns around online privacy and data security

Why Remote Desktop Software Matters in 2025 As remote and hybrid working

How do software teams consistently deliver applications that are reliable, secure, and

Is your computer running slower than usual or are certain devices not

Have you ever received a suspicious email or SMS urging you to

How do cybercriminals breach even the most secure systems without writing a

Platform as a Service (PaaS) is reshaping how software applications are developed

The demand for scalable, modular, and adaptable software has become the cornerstone

In today’s highly digitalised world, cloud computing is an indispensable tool for

In today’s increasingly connected world, the ability to access a computer remotely
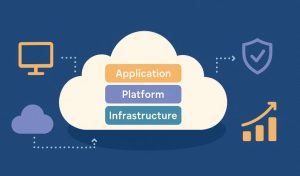
In today’s hyper-connected world, cloud computing powers nearly every digital service, from

Have you ever saved a document online or used an app without

In the ever-evolving digital economy, cloud computing has emerged as a transformative

In the ever-evolving world of technology, understanding the basics is often overlooked,